Our Commitment
The threat of cyberattack is constant for small businesses and major corporations alike. It’s almost always a question of when — not if — for your smart building.
That’s why we’re ready with a rapid response — whether you alert us to potential cybersecurity issues, or we spot them in our continuous diagnostics of the software and components we deploy. Whatever the situation, we’ll remediate vulnerabilities and address concerns with speed, professionalism, and transparency.
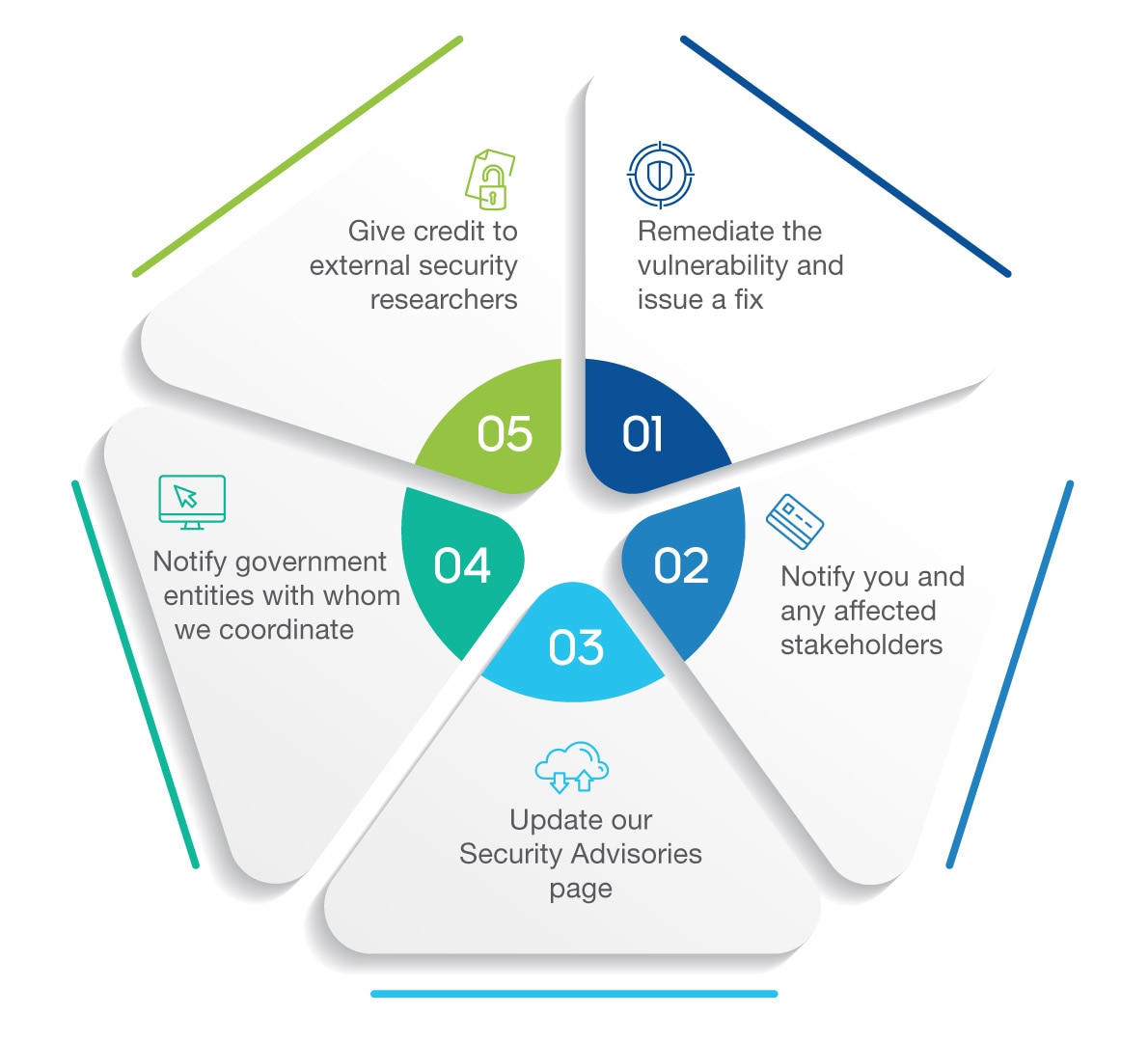
We respond to cybersecurity incidents with a disciplined process that limits your smart building’s exposure by assessing impact, protecting security interests, and coordinating disclosure.
Here’s how the process works when there’s a problem:
Wall of Thanks
The cybersecurity community includes independent researchers who work with us to identify vulnerabilities we can promptly correct. Johnson Controls want to acknowledge the importance of their contributions as they help us keep your systems and data as secure as possible.
2024 - Cybersecurity Community Researchers

2023 - Cybersecurity Community Researchers

2022 - Cybersecurity Community Researchers

2021 - Cybersecurity Community Researchers

Related Items
Coordinated Vulnerability Disclosure
We welcome reports from independent security researchers who believe they’ve found high or critical vulnerabilities in a Johnson Controls product — and with whom we work in partnership to address vulnerabilities using a Coordinated Vulnerability Disclosure process.
Following this process, we can protect customers by addressing potential vulnerabilities and planning a disclosure date after a fix is made available.
If a reported vulnerability involves a vendor’s product, we will notify that vendor directly, coordinate with the reporting entity, or engage a third-party coordination center.
Report Potential Vulnerabilities, Concerns or Inquiries
Cybersecurity testing may be conducted on Johnson Controls solutions. We recommend that tests are conducted in a non-production test environment to protect against disruption to operations.
A security test may produce field correctable findings if the steps outlined in the associated product Hardening Guide (Resources) are not followed.
Before conducting security tests, fully execute steps in the Hardening Guide (Resources). The following hardening steps, if not conducted, are known to result in addressable security findings:
- Update components to the most current supported release/version, and patch level that you are licensed to use, including:
- All Johnson Controls Applications
- All supporting software, not installed by Johnson Controls Applications, such as Windows, SQL Server, .NET and others
- Disable unused features, services, ports and software
- Install PKI certificates for applicable interfaces that are either:
- Provided by the local IT PKI administrator
- Acquired from a public Certificate Authority (CA)
- Before removing components not required by the Johnson Controls applications (e.g. old versions of Microsoft .NET, SQL and others):
- Ensure the software is not needed for any other function
- Ensure all data was properly migrated to the new Server instance
If a test tool detects potential issues with a Johnson Controls component, you may share the results with Johnson Controls or report other cybersecurity concerns at this link - https://www.johnsoncontrols.com/trust-center/cybersecurity/security-advisories#ReportAVulnerability, you may also contact us at productsecurity@jci.com.
Please use our downloadable PGP key to secure communications.

















.jpg?la=en&h=320&w=720&hash=244C75B74F0F77521D56164450973BCD)














.jpg?la=en&h=310&w=720&hash=8D9823F26AA80B2B75C3E4B2E61770DC)


.jpg?la=en&h=320&w=719&hash=13CA7E4AA3E453809B6726B561F2F4DD)
.jpg?la=en&h=306&w=720&hash=F21A7CD3C49EFBF4D41F00691D09AEAC)

.png?la=en&h=320&w=720&hash=18CFCCD916C92D922F600511FABD775D)















