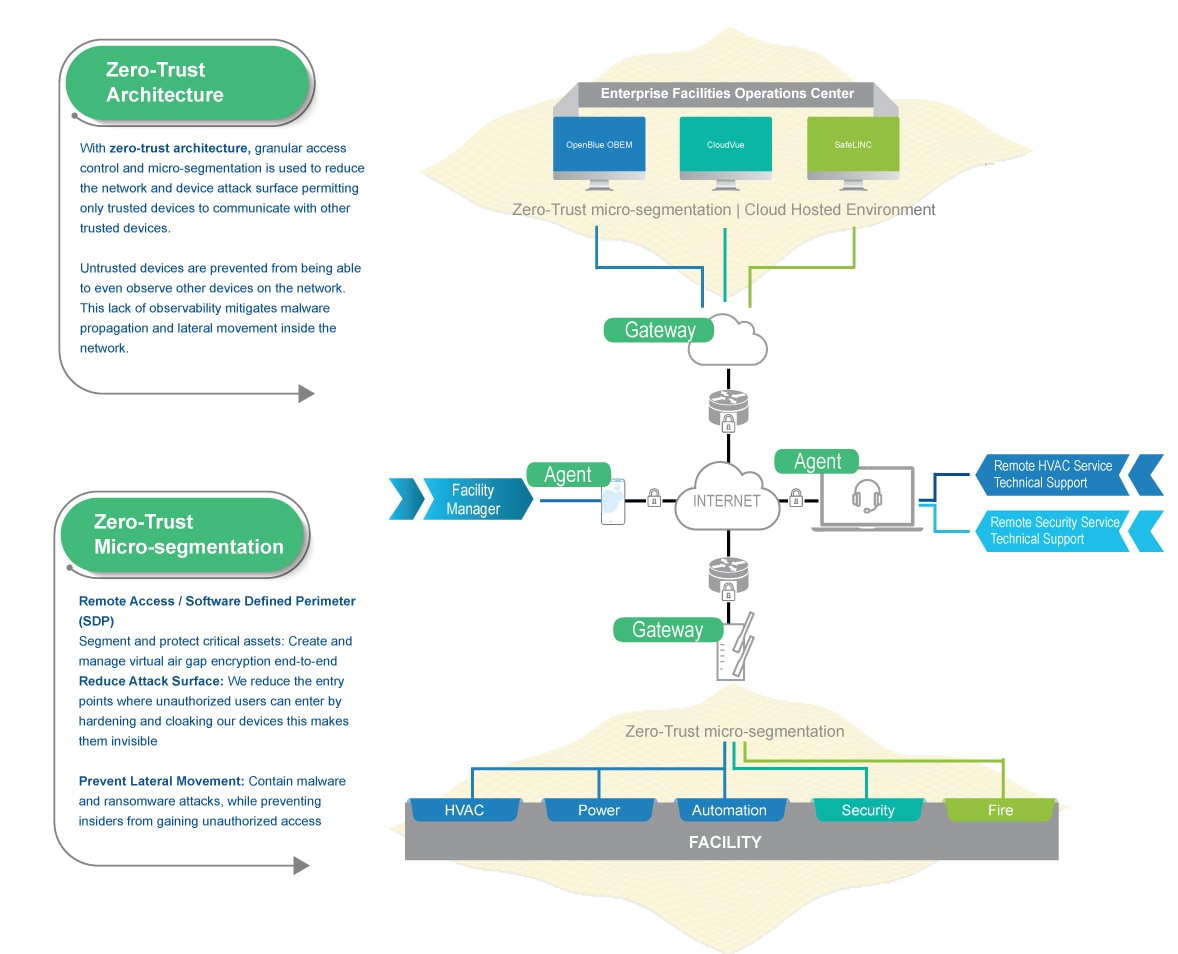
Zero-trust architecture
With zero-trust architecture, granular access controls and micro-segmentation is managed to reduce the attack surface and provides protection against unauthorized access, lateral movement and malware propagation.

Data Centers

Our data center infrastructure helps to streamline operations with increased uptime to achieve critical business goals.
Learn moreYour gateway to your sustainability and business goals

Digital solutions that improve energy efficiency, reduce carbon emission, optimize space use and equipment performance, and ensure health and wellbeing of occupants.
Learn more.png)
When organizations deploy OpenBlue in their buildings, they experience significant energy and cost savings, get more out of their real estate and report increased asset and shareholder value.
Learn more
Achieve decarbonization and renewable energy targets and optimize building performance.
Learn more
Indoor air quality is essential for the well-being, health, and productivity of the people inside every building, new and old.
Learn more
Optimize the performance of your building with OpenBlue, a complete ecosystem of connected technologies, expertise and services.
Learn more about OpenBlue
Unlock the performance of your building and provide real-time data visibility across assets, people, and processes with OpenBlue Enterprise Manager.
Learn more about OpenBlue
Funding more than $6B in customer projects worldwide, we partner with you to determine the best way to make your project happen.
Explore Johnson Controls Capital
Funding more than $6B in customer projects worldwide, we partner with you to determine the best way to make your project happen.
Explore Johnson Controls Capital
Funding more than $6B in customer projects worldwide, we partner with you to determine the best way to make your project happen.
Explore Johnson Controls capital
Our company has been the innovation leader, transforming and shaping the industry for 140 years. As we mark this milestone, we remain focused on what's ahead -- driving the next era of transforming industries and powering our customers' missions.
Learn moreAs part of OpenBlue — and built on our deep experience and customer focus — our products and solutions help you manage cybersecurity risks for your smart buildings.
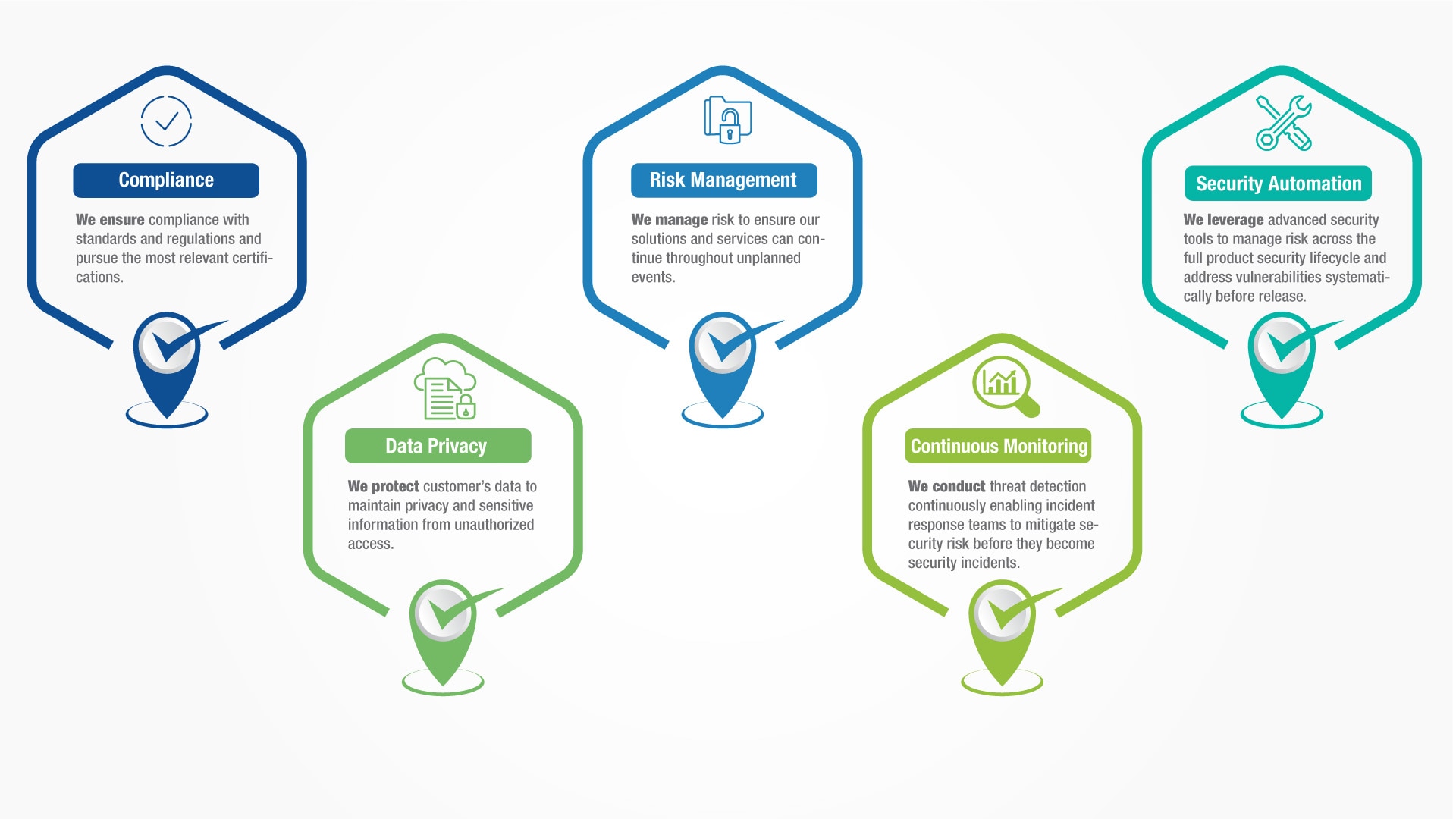
Johnson Controls products are developed using a secure-by-design approach. Security features for each solution are selected based on the application and environment they are targeted for.
Here are just a few examples of the advanced safeguards and assurances you can find within our solutions:

With zero-trust architecture, granular access controls and micro-segmentation is managed to reduce the attack surface and provides protection against unauthorized access, lateral movement and malware propagation.
Remote Access/Software Defined Perimeter (SDP):

Conformance with IEC/ISA 62443-4-2 ensures that product and solutions have sufficient safeguards within the software applications and embedded devices have sufficient safeguards according to appropriate security levels.
Examples: York Chillers, ISASecure CSA for Chillers

Federal Information Processing Standard (140-2) specifies the security requirements that will be satisfied by a cryptographic module, providing for increasing, qualitative levels intended to cover a wide range of potential applications and environments.
Examples:
Metasys, iSTAR Door Controller




Johnson Controls creates solutions which respect global fair information practices and Privacy by Design.





OpenBlue is a complete suite of connected smart building solutions, from edge to cloud. OpenBlue and other cloud-based solutions from Johnson Controls hosted in Microsoft Azure, Google Cloud or Amazon Web Services are protected environments that conform to industry recognized standards, such as:
Additional security compliance information for these environments is available at:



For everything from asking a question to raising an alarm, please use this form for a quick response from our Johnson Controls cybersecurity organization.
Report a potential vulnerability or cybersecurity concern | Ask about Products and Services | Learn about protecting your smart building
Cybersecurity testing may be conducted on Johnson Controls solutions. We recommend that tests are conducted in a non-production test environment to protect against disruption to operations.
A security test may produce field correctable findings if the steps outlined in the associated product Hardening Guide (Resources) are not followed.
Before conducting security tests, fully execute steps in the Hardening Guide (Resources). The following hardening steps, if not conducted, are known to result in addressable security findings:
If a test tool detects potential issues with a Johnson Controls component, you may share the results with Johnson Controls or report other cybersecurity concerns at this link - https://www.johnsoncontrols.com/trust-center/cybersecurity/security-advisories#ReportAVulnerability, you may also contact us at productsecurity@jci.com.
Please use our downloadable PGP key to secure communications.

