Cybersecurity for smart buildings
You want to protect your smart building — and Johnson Controls is here to help you.
Facility managers today require their smart building solutions to be cyber-resilient. We have developed a full lifecycle approach and set of security practices that can help you protect your building from a range of potential cyber threats.
How do we do it? Our expert cybersecurity team designs, deploys, and services your building’s connected systems — aligned to your security program, creating a layered defense for information, products, and privacy that’s ready for rapid response as issues arise.
Johnson Controls is setting the industry standard with digital products and services designed for smart buildings. As a leader in this space we continually earn your trust by helping you achieve business outcomes while managing risk.
Johnson Controls takes a holistic, structured approach to help you protect systems and sensitive data from the risk of a cyber-attack. Powering impactful sustainability, safety and security, we deliver an enhanced customer experience.
How we protect you

Products and solutions
As part of OpenBlue, we tailor Cybersecurity to your precise needs — helping you protect your smart building’s systems and data from the threat of cyberattack.

Practices
Our holistic, structured approach uses cyber-resilient products and services to maintain a robust security posture, information security, product security, and privacy for your smart building.

Response
A strong offense is just as important as a strong defense. As we proactively monitor the dynamic threat landscape and address risks, we’re ready with rapid response to security incidents.

Resources
We continuously enhance our products and security guidelines — and partner with you in managing cybersecurity risk by sharing valuable information and best practices.

Product security advisories
We track, identify, and address cybersecurity threats on a daily basis. As part of our commitment to transparency we keep you informed of security concerns and important Johnson Controls product updates.

OpenBlue
OpenBlue is a complete suite of connected solutions that serves industries from workplaces to schools, hospitals to campuses and more. Our cybersecurity solutions are designed to keep your spaces safe and secure.
Johnson Controls approach to secure product development, support and service
Johnson Controls designs cybersecurity into our product and solution offerings and endeavors to protect those solutions (including software, hardware and hosted services) to protect your data and operations across the risk management lifecycle. Our secure product practices include the design, sourcing, development, deployment, servicing, support and retirement of products. All new Johnson Controls commercial products are developed under governance of our cybersecurity policies, standards and guidelines, which includes requirements for product testing and vulnerability management.
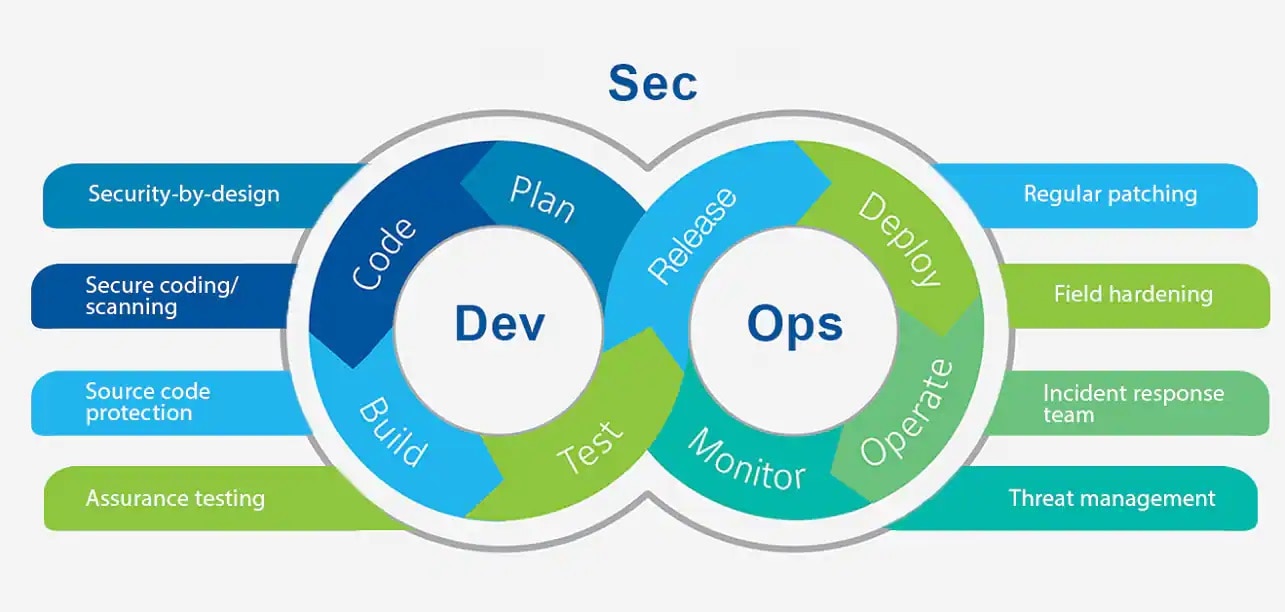
Johnson Controls proactively manages cybersecurity and privacy risks. We have dedicated organizations governing product security, information security, and data privacy. These organizations work together to deliver high-quality and consistent cybersecurity and data privacy support in a way that meets the unique mission and technology needs of each customer. Powering our customers’ mission is our top priority, and that means doing our part to protect our customers’ sensitive data and operations. Our rigorous secure product development lifecycle, agile DevSecOps practices, and approach to field operations cybersecurity strengthen our ability to meet that commitment. Additionally, our unified security and privacy controls framework is structured to ensure compliance with laws and regulatory requirements, globally.
Alliances and partnerships
It’s more than deep experience protecting smart buildings like yours — it’s continuous innovation as we protect their systems and data from new and evolving threats. That’s why we work in close collaboration with international government agencies, industry peers, and cybersecurity experts to keep our products and services at the leading edge of cyber resilience. We encourage you to learn more about our alliances and partnerships:
Johnson Controls is a founding member of the International Society of Automation’s Global Security Alliance (GCA).
Johnson Controls is a strategic voting member of ISA Secure Compliance Institute. Johnson Controls conforms to the ISA/IEC 62443 Standard.
See what's new in Johnson Controls
See all insights

How can we help you?
For everything from asking a question to raising an alarm, please use this form for a quick response from our Johnson Controls cybersecurity organization.
Report a potential vulnerability or cybersecurity concern | Ask about products and services | Learn about protecting your smart building
Cybersecurity testing may be conducted on Johnson Controls solutions. We recommend that tests are conducted in a non-production test environment to protect against disruption to operations.
A security test may produce field correctable findings if the steps outlined in the associated product Hardening Guide (Resources) are not followed.
Before conducting security tests, fully execute steps in the Hardening Guide (Resources). The following hardening steps, if not conducted, are known to result in addressable security findings:
- Update components to the most current supported release/version, and patch level that you are licensed to use, including:
- All Johnson Controls Applications
- All supporting software, not installed by Johnson Controls Applications, such as Windows, SQL Server, .NET and others
- Disable unused features, services, ports and software
- Install PKI certificates for applicable interfaces that are either:
- Provided by the local IT PKI administrator
- Acquired from a public Certificate Authority (CA)
- Before removing components not required by the Johnson Controls applications (e.g. old versions of Microsoft .NET, SQL and others):
- Ensure the software is not needed for any other function
- Ensure all data was properly migrated to the new Server instance
If a test tool detects potential issues with a Johnson Controls component, you may share the results with Johnson Controls or report other cybersecurity concerns at this link - https://www.johnsoncontrols.com/trust-center/cybersecurity/security-advisories#ReportAVulnerability, you may also contact us at productsecurity@jci.com.
Please use our downloadable PGP key to secure communications.

























.png?la=en&h=70&w=157&hash=717A494A27ED61C45CEF95AC3A9C6309)